SOEN 321 Project
SOEN 321 Winter 2019
Topic 6 DNS Interception Study
Who Is Answering My Queries
What need to do
- Set a few free domains
- Use a residential proxy service like the authors - instead you can also start with free hosting services
- Attempt to replicate as much as you can from the paper (exclude the China part)
What is in the article
Terminology
- ISPs: Internet Service Providers
- DNS: Domain Name System, resolving human-readable names to numerical IP addresses
- DNS transparent proxy
- Web proxies work by intercepting a request, modifying the request if necessary, then handling or forwarding the request to its destination. Proxies allow service providers to shape and optimize the way users connect to their services, but they also allow network providers to impact the way users or employees access external resources.
- Traditionally, proxies are accessed by configuring the user’s application or network settings.
- With transparent proxying, the proxy intercepts requests by intercepting packets directed to the destination, making it seem as though the request is handled by the destination itself. This allows service providers to implement proxying without having to reconfigure the user’s computer.
- What is a Transparent Proxy?
- ASes: Autonomous Systems
- DNSIntercept: hidden interception of the DNS resolution path
- TLD: Top-Level Domains
- SLD: Second-Level Domains
- FQDN: a fully qualified domain name
1. Introduction
How
- DNS queries from end users are handled by recursive DNS servers for scalability.
The concerns rasied from DNS interception:
- The interception is not authorized by users and is difficult to detect on the users’ side, which leads to ethical concerns;
- Users have higher risks to put the resolution trust to alternative recursive DNS servers, which often lack proper maintenance (e.g., equipped with outdated DNS software), compared to well-known public DNS servers;
- Certain security-related functionalities are affected or even broken, e.g., some alternative DNS resolvers do not provide DNSSEC.
Challenges:
- Acquire clients belonging to different ASes to perform a large-scale measurement, which also should allow fine-tuning on the measurement parameters. Advertising networks, HTTP proxy networks, and Internet scanners cannot fulfill the conditions at the same time.
- Verify whether the DNS resolution is intercepted rather than reaching users’ designated recursive nameservers. Since on-path devices are able to spoof the IP addresses in the DNS responses, it is difficult to sense the existence of DNS interception merely from the clients.
Approaches
- Devise a new measurement methodology.
- Register a set of domains (e.g., OurDomain.TLD), and use the authoritative nameservers controlled by us to handle resolutions.
2. Threat Model and Mechanisms
Domain Resolution Process
- FQDN:
www.example.com - SLD:
example.com - TLD:
com
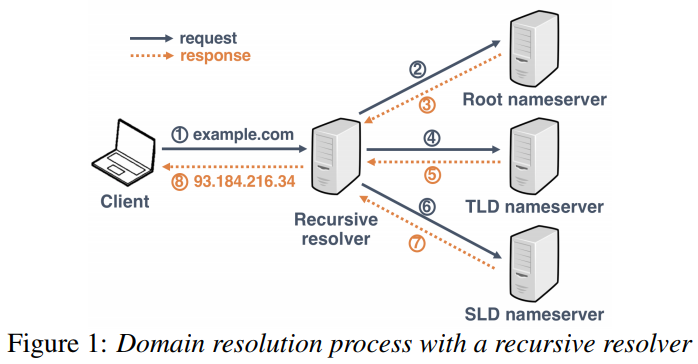
- FQDN:
Threat Model
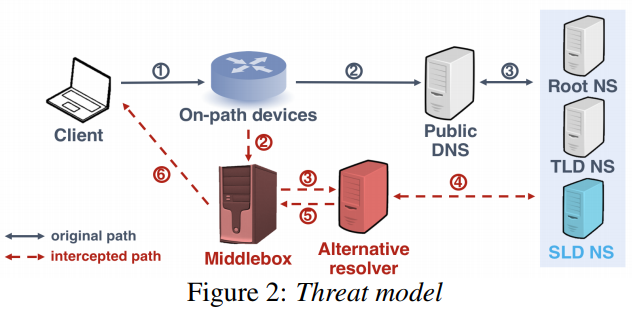
- redirect or replicate the requests to alternative resolvers
- before responses are sent from alternative resolvers back to clients, the sources are replaced with addresses of the original resolvers.
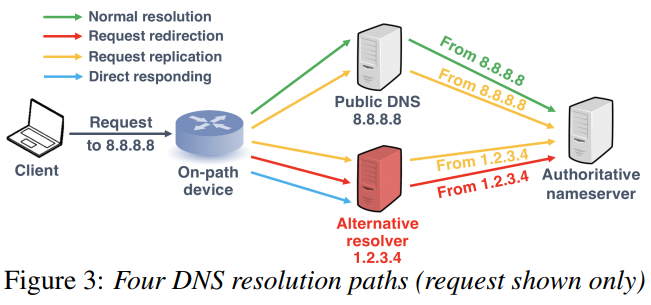
- Taxonomy of DNS resolution paths:
- Normal resolution
- Request redirection
- Request replication
- Direct responding
Potential Interceptors
- Censor and firewall
- Malware and anti-virus (AV) software
- Enterprise proxy
3. Methodology and Dataset
- Overview
- Approach
- instruct a client to send a DNS request about one of our controlled domains to a public resolver A;
- record its corresponding request at our authoritative nameservers, which originates from recursive resolver B; and
- compare A with B. As a complementary step, we also
- validate the response eventually received by the client.
- Approach
- Methodology
- DNS packet: {Src IP, Dst IP, Protocol, RR Type, Requested Domain}
- Generate DNS requets: UUID.Google.OurDomain.TLD, UUID should be distinct.
- Generate DNS responses
- Identifying egress IPs of public DNS
- Vantage points
- Dataset
DNS Profiling (Python)
Source code
Steps
- Domains are fetching from website global topsites and category topsites
- Use
BeautifulSoupto crab the webpage to get the domains of top websites. - Write these records to files
top-world-%yyyyMMdd%andtop-categories-%yyyyMMdd%. - Get the list of the countries of so-called the enemy of Internet from wikipedia
- Search these countries' DNS from web.
- Use these DNSs to query the domains which fetched from the third step.
- Log the response to
output-%yyyyMMdd%file. - Total DNSs, domains, records.
Next
- Add custome domains
- Confirm unuseful DNS
- Statistics