SOEN 321
SOEN 321 Winter 2019
Outline
- Instructor: Dr. Mohammad Mannan
- Outline
Final
- Set 3: Stream cipher
- Set 4: Block cipher
- Set 5: Hash
- Set 6: MAC
- Set 7: PKI-SSL
- Set 8: Usability
- Set 9: Botnets-DDos
- Set 14: Inuksuk
Cheatsheet
| Name | Block size | Key size | Output size | Rounds |
|---|---|---|---|---|
| DES | 64 | 56 | 16 | |
| AES-128 | 128 | 128 | 10 | |
| AES-192 | 128 | 192 | 12 | |
| AES-256 | 128 | 256 | 14 | |
| SHA1 | 160 | |||
| SHA2-256 | 256 |
0. Preparation
0.1 Modulus
- implies: divides
- implies:
- e.g.: ,
0.2 Pseudo-Random Number Generators (PRNG)
- Definition
- A given PRNG is a deterministic function that takes a fixed-length key (seed) and produces anunbounded bit stream.
- Same seed (entropy source), same sequence
- Hardware vs. Software sources
- Sound/video input, disk drives
- Elapsed time between emission of particles during radioactive decay
- Linux (/dev/random)
- Mouse, keyboard activities
- Disk I/O
- Interrupts
- Embedded devices / IoTs
- CPU support
- Online service (should note be trusted)
- Produces “statistically random” numbers
- it passes standard tests for randomness
- Cryptographically secure, if
- Unpredictable (next-bit test): computationally infeasible to predict the next bit given a complete history of past bits.
- Balanced: The number of ’s and ’s should be equal.
0.3 Some Other Types of Security
Unconditional security:
- The uncertainty in the plaintext, after observing the ciphertext, must be equal to the a priori uncertainty about the plaintext. Observation of the ciphertext provides no information to an adversary.
Computational security:
- level of computation required to defeat it (using best attack known) >> the computational resources of the adversary.
- Data complexity is : is the block size.
- Processing complexity is : is the key size.
0.4 Attack analysis
- Complexity of an attack
- Data complexity– expected number of required input data units (ciphertext blocks).
- For a block of size , it is .
- Storage complexity – expected number of required storage units..
- Processing complexity – expected number of required operations on data.
- For a key of size , it is .
- Data complexity– expected number of required input data units (ciphertext blocks).
- How to reduce complexity
- possible parallelization
1. Trusting trust
1.1 Security stack
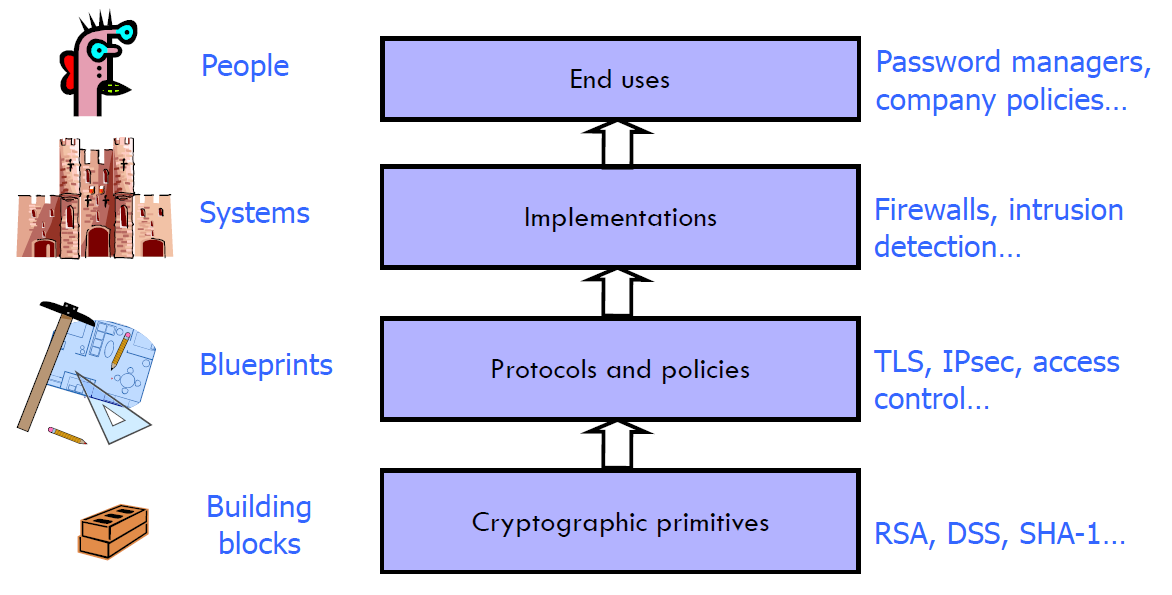
1.2 Security v.s. Correctness
- System security: System properties preserved in the face of an attack.
- System correctness: For reasonable input, get reasonable output.
1.3 What code to trust?
- Is Windows/OSX binary reliable?
- No. So we use open-source, or wirte our own.
- But we need to compile.
- Who wrote the compiler?
- So inspect the source code of the compiler, and recompiler the compiler.
- But there is another compiler.
"The moral is obvious. You can't trust code that you did not totally create yourself."
1.4 Examples
- The Bullrun project
- The PRISM Program
1.5 Security Mindset
“Think like an attacker, but do not attack.”
2. Cryptography
Cryptography Security
2.1 What Cryptography is
Cryptography is the study of mathematical techniques related to aspects of information security such as confidentiality, data integrity, entity authentication, and data origin authentication.
- Always think from three perspectives
- Defenders' view point
- Attackers' view point
- How much it will cost – to protect & to attack
2.2 What Cryptography for
- Confidentiality: prevent others from reading a message
- Integrity: someone didn’t replace or modify a message
- Data origin authentication: a message originated from a certain source
- Entity authentication: a person is who he/she claims to be. e.g.: password
- Non-repudiation: prevent someone from denying past commitments or actions; that is, someone cannot deny the validity of something.
2.3 Cryptology
- Cryptology = Cryptography + Cryptanalysis
- Cryptanalysis: Study of code breaking
2.4 Basic tools of cryptography: Security Primitives
- Unkeyed Primitives
- Hash functions
- One-way permutations
- Random sequences
- Symmetric-key Primitives
- Symmetric-key ciphers
- Block ciphers
- Stream ciphers
- Message Authentications Codes (MACs)
- Signatures
- Pseudorandom sequences
- Identification primitives
- Symmetric-key ciphers
- Public-key Primitives
- Public-key ciphers
- Signatures
- Identification primitives
2.5 Attacker model
- Passive vs. active attacker
- What computational resources the attacker has?
- What does the attacker know about a system?
- What are the assumptions?
- encryption keys are shared via a secure channel
2.6 Encryption
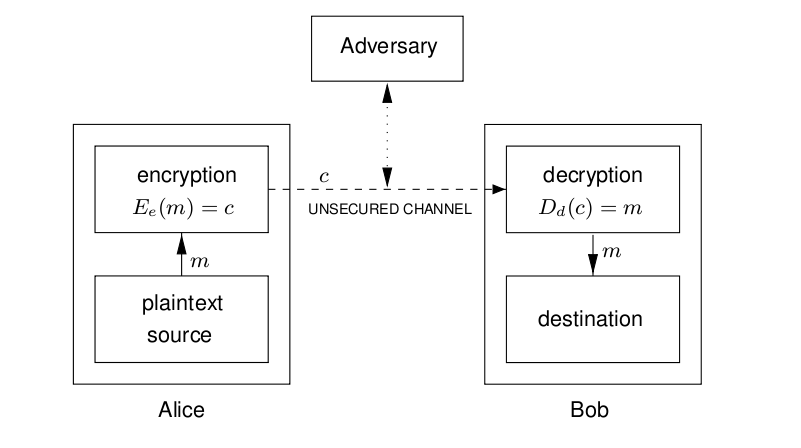
- Goals
- Data confidentiality
- Protect a large amount of data with "short" secrets, like a lock-and-key.
- Make it difficult for those without the secret key; efficient retrieval with the correct key.
- Simple model
- What to hide: key + plaintext
- Terminologies
- plaintext - the original message, denoted or
- ciphertext - the encoded message, denoted
- cipher - algorithms for transforming plaintext to ciphertext and vice-versa
- key - info used in cipher known only to sender/receiver
- encipher (encrypt) - converting plaintext to ciphertext, denoted
- decipher (decrypt) - recovering ciphertext from plaintext, denoted
- substitution – each element is mapped into another
- transposition – rearrangement of elements
- Kerckhoff’s Principle
- Security should depend only on the key
- Don’t assume enemy won’t know algorithm
- Can capture machines, disassemble programs
- Too expensive to invent new algorithm if it is compromised
- Security by obscurity does not work
- Security should depend only on the key
- History
- Classical ciphers
- Pen & paper, simple mechanical machines
- Egyptians, Greeks, Romans, Hebrew scholars
- World War I
- Vernam Cipher (one time pad)
- World War II
- Complex electro-mechanical machines
- Enigma
- Modern crypto
- Depends on – computers, math
- Data Encryption Standard (DES) – 1975
- Public key systems – 1976
- Common people use
- Classical ciphers
2.7 Examples
1. Substitution ciphers
- How it works
- Each symbol in plaintext is replaced by another symbol according to some fixed permutation
- e.g.: Repalce by , by .
- For a set of English characters, all possible mappings is .
- But such a large key space does not mean it is secure (why? Pattern).
- Each symbol in plaintext is replaced by another symbol according to some fixed permutation
- Substitution is said to add confusion (makes relationship between key and ciphertext as complex as possible)
- Break it: Brute force key search
- English letter frequencies
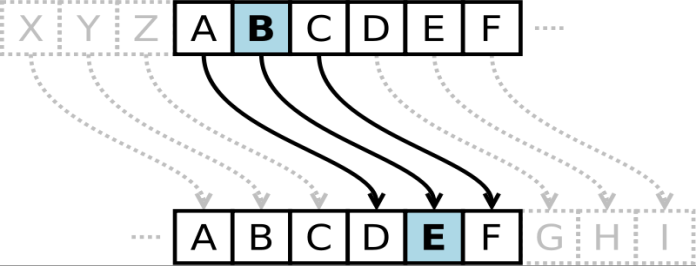
Shift/Caesar cipher
- How it works
- It is one type of simple substitution cipher.
- Shift each letter by an offset.
- For a set of English characters, all possible mappings is .
- Break it: Brute force
- Only keys
Polyalphabetic substitution
- How it works
- Multiple substitution alphabets
- Vigenère cipher
- Enigma
- Pick a keyword, repeat it to mapping plaintext.
- Lookup in the table using the keyword letter and its conresponding plaintext letter.
- Multiple substitution alphabets
- Transposition is said to add diffusion (spreading out bits so redundancy in plaintext is spread over ciphertext), so more resistant to frequency analysis.
- Break it
Transposition cipher
- How it works
- With a fixed period ,
- grouping the plaintext into blocks of characters,
- applying to each block a single permutation on the numbers to .
- e.g.:
2. Block & stream ciphers
Block cipher
- plaintext message is broken into fixed-length blocks before encryption
- one block is processed at a time
- most modern ciphers are block ciphers
Stream cipher
- block length is one
- requires only limited buffering of data
2.8 How to attack encryption
- Cryptanalysis
- Search for weaknesses in the algorithms
- (Partial) knowledge about plaintext, ciphertext
- Brute-force
- Try all possible keys ()
- On average trails are required
- Malware, key/screenlogger, physical and side-channel attacks...
Attacks on encryption schemes
- Ciphertext-only attack - deduce the decryption key or plaintext by only observing ciphertext
- Known-plaintext attack - using a quantity of plaintext and corresponding ciphertext
- Chosen-plaintext attack - choose plaintext and is then given corresponding ciphertext
- Adaptive chosen-plaintext attack - chosen-plaintext attack where the choice of plaintext may depend on the ciphertext received from previous requests
- Chosen-ciphertext attack - select the ciphertext, then the corresponding plaintext is given
- Adaptive chosen-ciphertext attack - chosenciphertext attack where the choice of ciphertext may depend on the plaintext received from previous requests
3. Stream ciphers
- Synchronous stream ciphers
- Key-stream is generated independently of plaintext and of ciphertext
- Self-synchronizing stream ciphers
- Key-stream is generated as a function of the key and a fixed number of previous ciphertext digits
- Examples:
- Vernam cipher
- One-time pad
- RC4
- ChaCha20
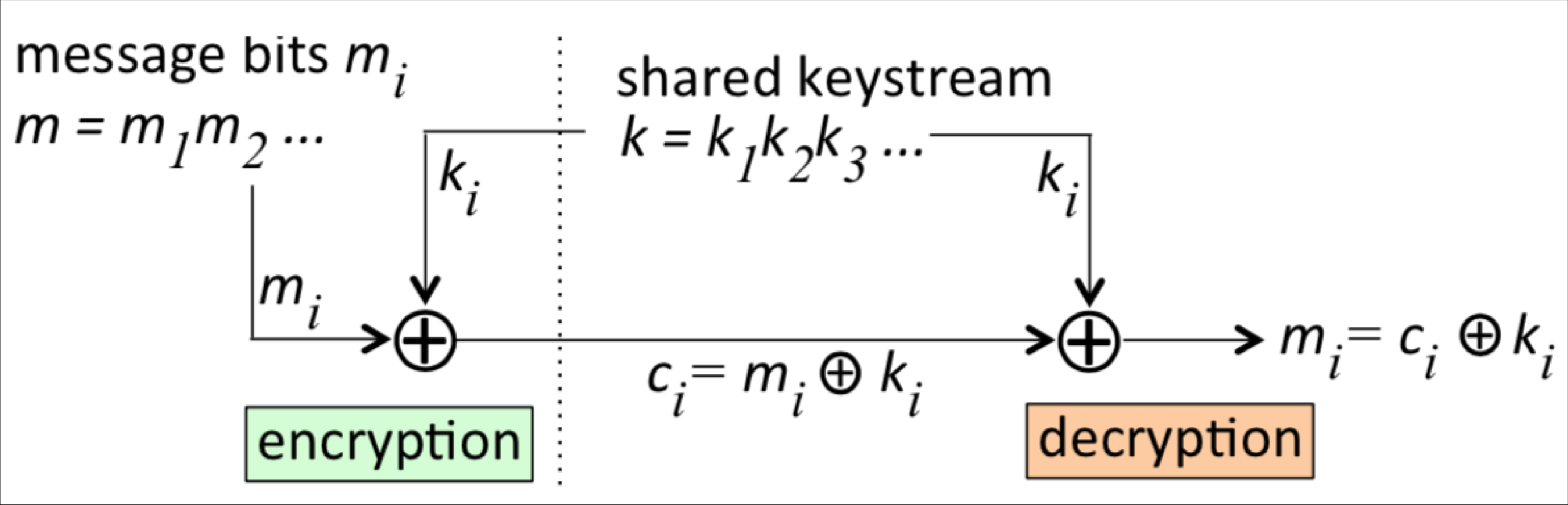
3.1 Vernam Cipher
- How it works
- Plaintext:
- Key string:
- Cipertext:
3.2 One-time pad
Why we need it
- Vernam cipher "can" use any bit source as a keystream,
- But for real security the key should be random and never use again.
- Vernam cipher with such a key-stream is called a one-time pad.
- The one-time pad is provably secure.
- One-time pad is unconditionally secure against a ciphertext-only attack, observation of the ciphertext provides no information to an adversary.
How it works
- Same as vernam cipher
What if
Reuse the key-steam
If ciphertexts and one plaintext are known.
Not random
- Brute-force
Probability of and in ciphertext
- In the plaintext, assume the probability , then .
- Assume the probability of a key bit .
- Four cases:
- So:
- But:
- No integrity
3.3 RC4
- What it is
- Byte-oriented, fast in software
- Variable-length key: 40 – 2048 bits
- Similar to the one-time pad except that generated pseudorandom bits, rather than a prepared stream, are used.
- How it works
- Initialization: the permutation is initialized with a variable length key.
- Keystream: the stream of bits is generated using and two 8-bit index-pointers (denoted and ).
- , same as one-time pad.
3.4 ChaCha20 stream cipher
- What it is
- 256-bit key
- 96-bit nonce
- 32-bit block counter
- How it works
- Output a 64-byte block of key stream and increments block counter in each invocation
- If never use the same nonce with the same key twice, it is a one time pad.
- Output a 64-byte block of key stream and increments block counter in each invocation
4. Block ciphers (symmetric key)
- What it is
- A function that maps -bit plaintext blocks to -bit (blocklength) ciphertext blocks.
- If key is bits long, the number of keys is .
- Encryption:
- Decryption:
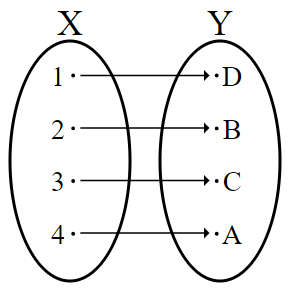
- The encryption function must be one-to-one (bijection).
- One-to-one: Because the encryption and decryption process must be reversed.
- Not onto: Some s have no correspoing s, so if a bit flip occurs, decryption would fail.
- Not one-to-one: Ambiguity, maps more than one .
- Used for
- Data confidentiality
- MACs
- PRNGs (pseudorandom number generators)
- Authentication
- Very efficient software and hardware implementations
- Can be used in low-resource devices
- Practical security
- Standard assumptions (in addition to Kerckhoff's):
- attacker has access to all transmitted ciphertext.
- A block cipher is:
- totally broken if key is recoverable, and
- partially broken if (some) plaintext is recoverable (without a key)
- Standard assumptions (in addition to Kerckhoff's):
- Modes of operation
- How to employ block ciphers for large messages
- Dividing messages
- Padding the last block
- Basic modes
- ECB: Electronic Code Book
- CBC: Cipher Block Chaining
- OFB
- CFB
- Initialization Vector (IV)
- A block of data used in addition to the input message
- Randomize the encryption process
- How to employ block ciphers for large messages
4.1 Electronic Codebook (ECB)
- Overview
- Same plaintext result in identical ciphertext
- Blocks are enciphered independently of other blocks
- Bit errors in a single ciphertext affect decipherment of that block only
- How to
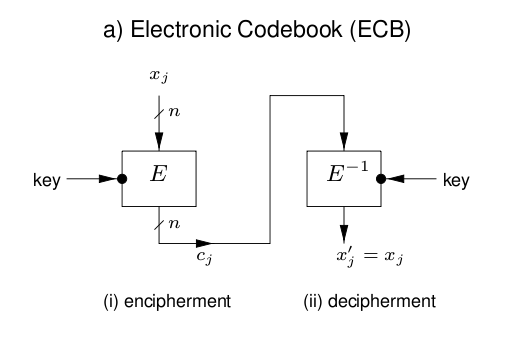
- Weakness
- Does not hide data patterns
- Malicious substition of ciphertext is possible

- Usage
- When can we use this mode:
- Plaintext that has size of less than one block, to avoid pattern
- When not to use it:
- Multi-block messages
- Key are reused more than a single block
- When can we use this mode:
4.2 Cipher Block Chaining (CBC)
Overview
- Chaining causes ciphertext to depend on all preceding plaintext
- Random access to encrypted data is not possible because of the previous reason.
- Also because of that, only the same key, IV, plaintext results identical ciphertext.
- IV must be integrity-proteced
- If not, attackers may make predictable bit changes to the 1st block.
- If your salary is saved as , you can flip the in IV corresponding to in your salary to change your salary to .
- A single bit error in affects decryption of blocks .
How to
- for ,
- for ,
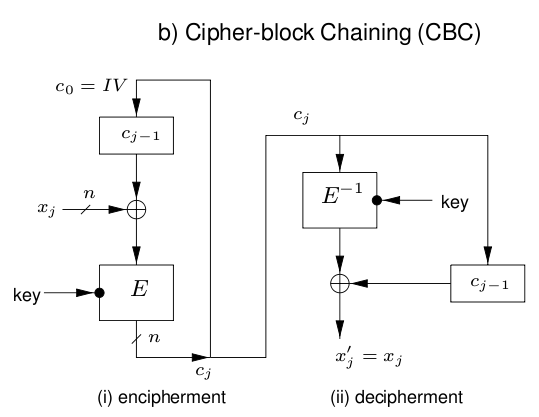
- Weakness
- Has known weaknesses?
4.3 Counter mode (CTR)
Overview
- CTR must be different for each block
- An IV/nonce value is also used with the counter for uniqueness (concat/addition/xor)
Advantage:
- Software and hardware efficiency: different blocks can be encrypted in parallel
- Preprocessing: the encryption part can be done offline and when the message is known, just do the XOR.
- Random access: decryption of a block can be done in random order, very useful for hard-disk encryption.
How to
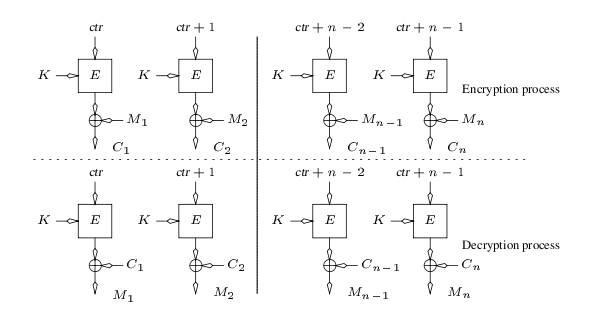
4.4 XTS-AES
- XEX (xor-encrypt-xor): efficient processing of consecutive blocks within a data unit.
- CTS (CipherText Stealing): provides support for sectors with size not divisible by block size.
- XTS: XEX-based Tweaked CodeBook mode (TCB) with CipherText Stealing (CTS).
4.5 ECB-CTS
- How to
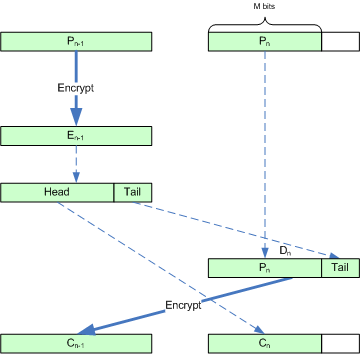
- Why //TODO
4.6 Block cipher: design components
Avalanche effect
- Slight change in input (e.g., flipping a single bit) significantly changes the output (e.g., half the output bits are flipped)
- Strongly desired property of:
- Block ciphers
- Cryptographic hash functions
Product cipher
- Execution of two or more simple ciphers in sequence (round of operations), such that the final product is cryptographically stronger than its components
- In particular, alternating substitutions and transpositions
Block cipher design approaches
- A round function is used
- Strong avalanche effect
- Bijective
- Repeated multiple times ( rounds)
- Round input: plaintext block
- Round output: ciphertext block
- Round key: derived fromthe key , for each round
- Examples
- SP networks (used in AES, CAST-128)
- Feistel structures (used in DES, RC5, Blowfish)
Substitution-permutation (SP) network
- How to
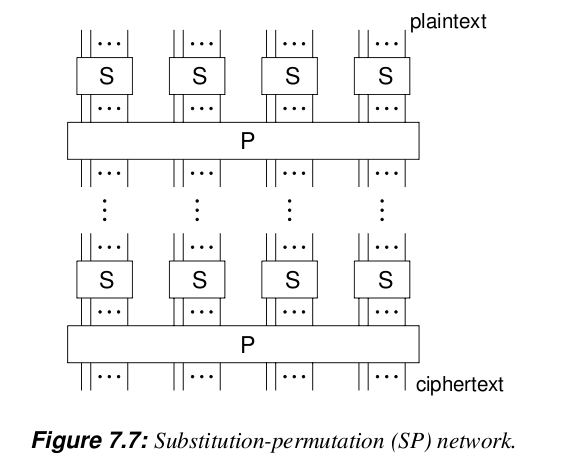
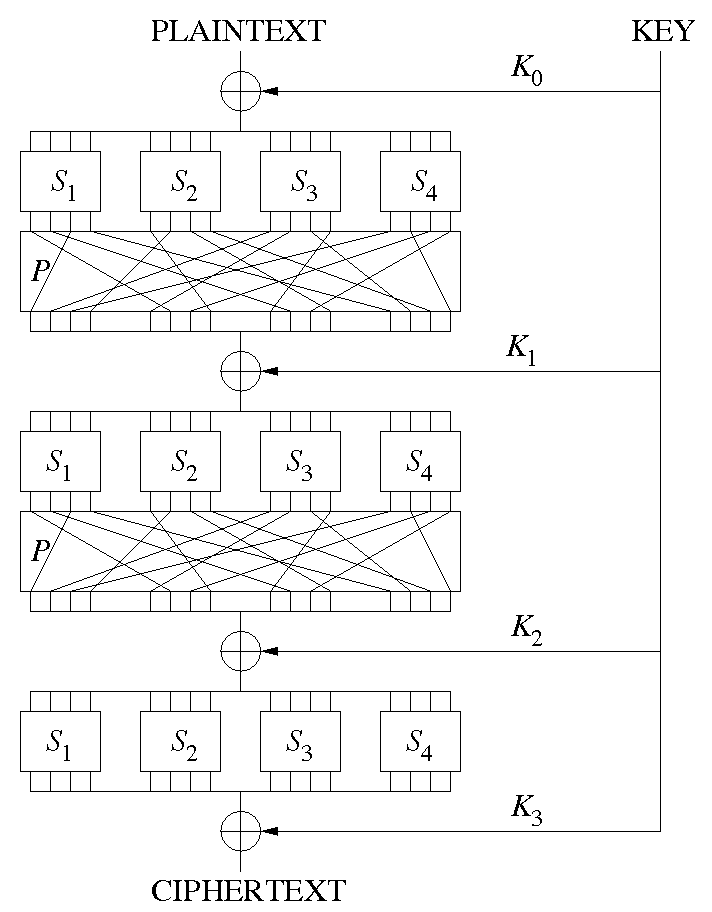
Feistel structure
Overview
- Consists of a number of identical rounds of processing
- In each round, a substitution is performed on 1/2 of plaintext block, followed by a permutation that interchanges two halves
- The original key is expanded so a different key is used in each round
- The Data Encryption Standard (DES) exhibits this structure
How to
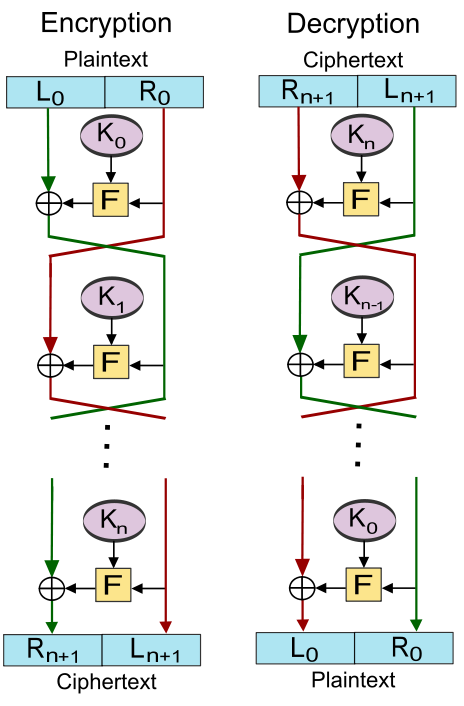
- Feistel structure parameters
- Block size & key size:
- larger means greater security, but may slow down encryption/decryption speed
- Number of rounds:
- more rounds means greater strength
- typically 16 rounds
- Subkey generation algorithm & round function:
- greater complexity should lead to greater cryptanalysis resistance
- Block size & key size:
4.7 Data Encryption Standard (DES)
- Overview
- Use the Feistel structure
- Block length , key size .
- Number of rounds is .
- Use the Feistel structure
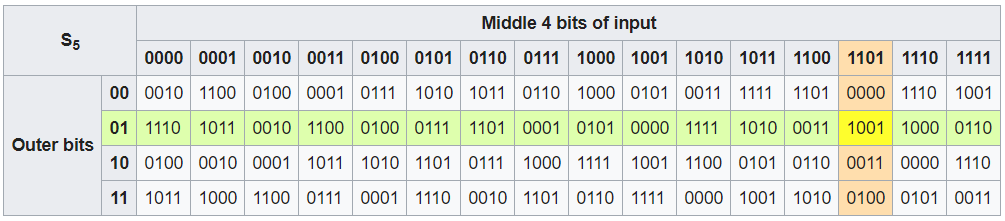
- S-box (substitution-box)
- Outer bits: two bits (the first and last bits)
- Inner bits: the other four bits between the first and last bits
- e.g.: , outer bits are , inner bits are .
Double/Triple encryption (DES)
The security of DES depends on its large key space.
Double encryption should double the size () of the key space?
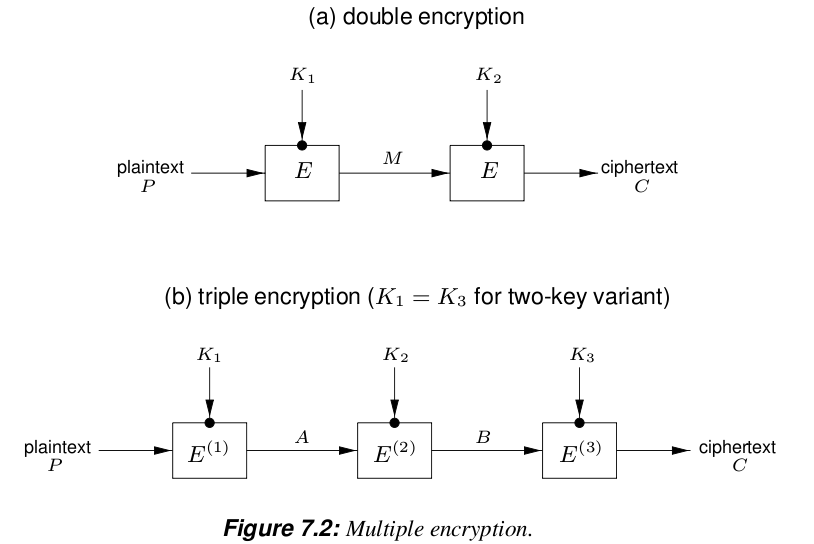
Meet-in-the-middle attack (DES)
Double-DES:
- Compute and store for all possible
- Compute and store for all possible
- Match
- Reduces key search from to at the expense of addition storage .
Triple encryption: Security of
Alternative to DES
- Double-DES - no security advantage
- Triple-DES - secure, but slow
- So, Advanced Encryption Standard (AES)
4.8 Advanced Encryptioin Standard (AES)
Overview
- Block length:
- Consider it as a matrix of bytes:
- Key length: AES-128 (n=10), AES-192 (n=12), AES-256 (n=14)
- Block length:
How to
Derive round kyes (KeyExpansion): State = X(input)
Initial round: AddRoundKey(State, ): State Expanded key
Rounds (Nr-1 times)
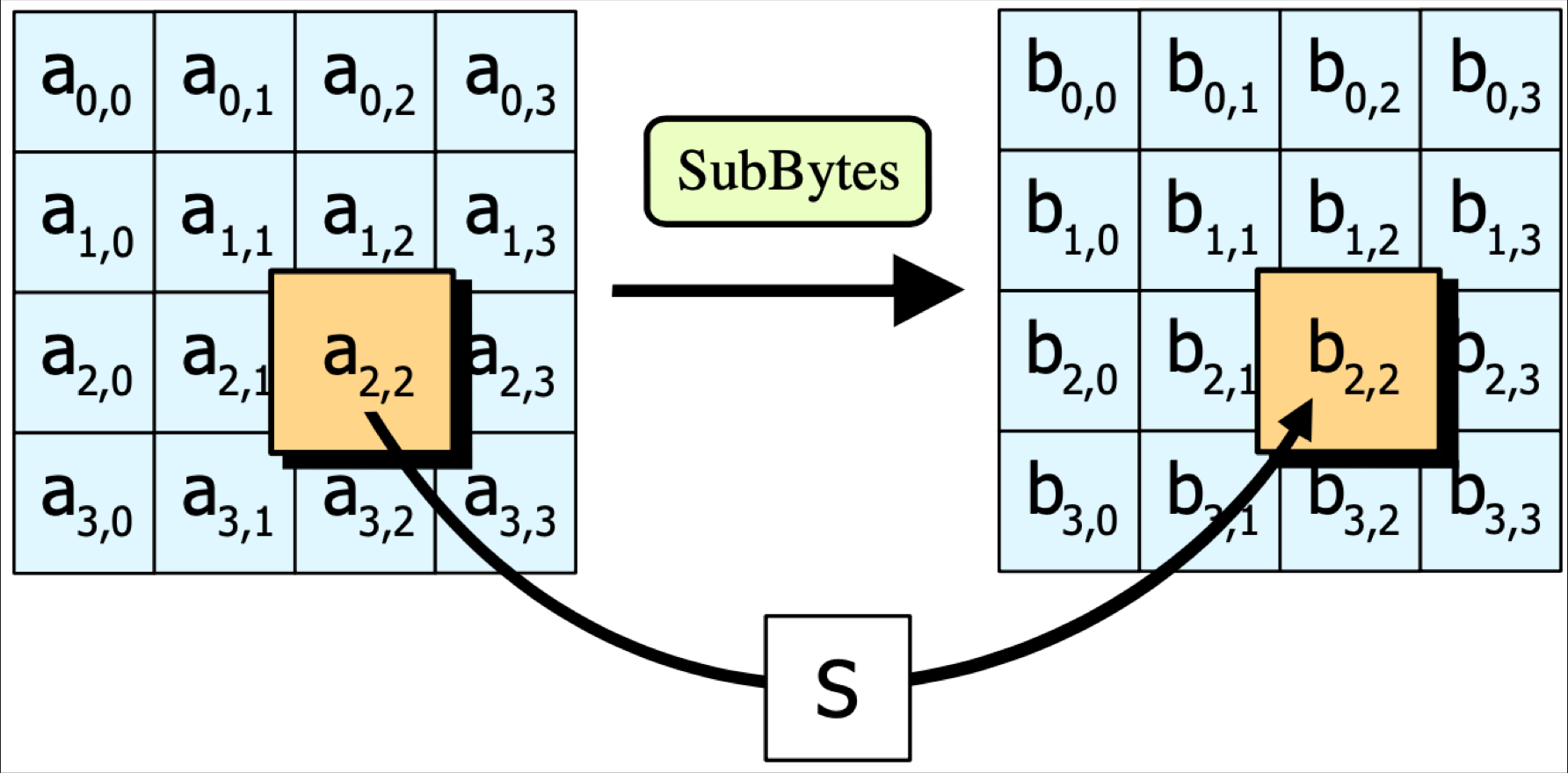
SubBytes(State, S-box): a substitution step
- Each byte in the state is replaced with its entry in a fixed 8-bit lookup table S (substitution box or S-box).
- Provides non-linearity.
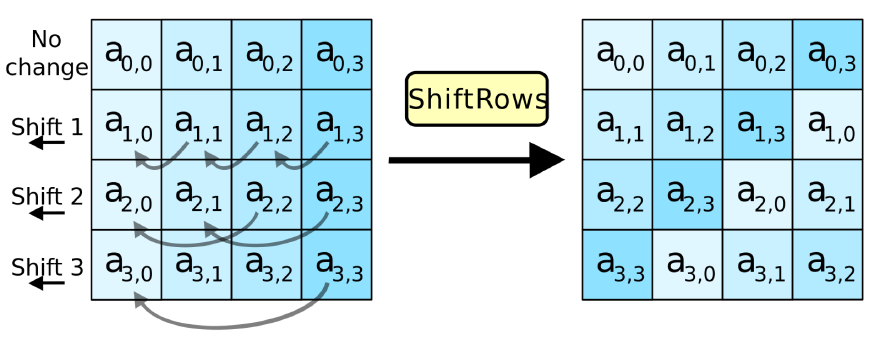
ShiftRows(State): a transpositioin step
- Avoid the columns being encrypted independently.
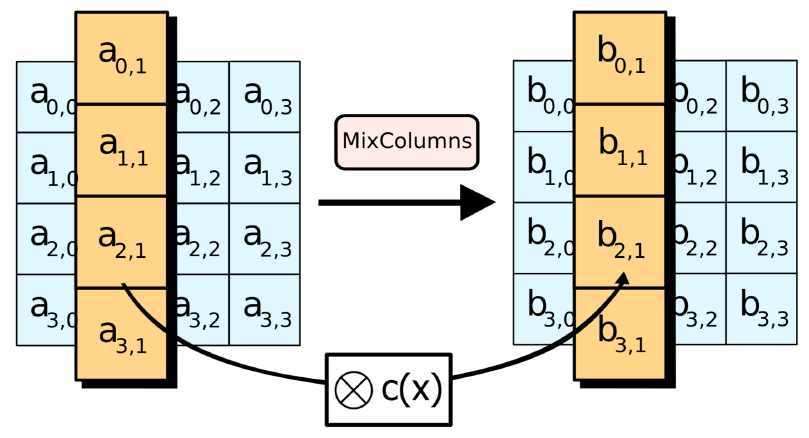
MixColumns(State):
- Each column of the state is multiplied with a fixed polynomial.
- Together ShiftRows, MixColumns provides diffusion.
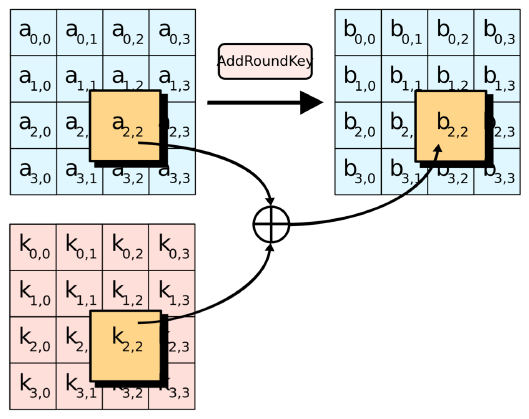
AddRoundKey(State, ):
- The round subkey is combined with the state using bitwise XOR
- For each round, a subkey is derived from the main key using Rijndael's key schedule
Final Round (no MixColumns)
- SubBytes
- ShiftRows
- AddRoundKey
Y(output) = State
Attack
- No practical attacks to date
- No attacks on full AES versions
5. Hash Functions
5.1 What it is
- Input: a string of arbitrary length, called the preimage.
- Output: a string of fixed length, called hash-value, hash-code, hash-result, or hash.
- Collsions: is a many-to-one function
- Assume to , and is random.
- input, output, so inputs would map to the same output.
- Collisions probability:
- Properties:
- Compression
- Ease of computation
- Pre-image resistance (one-way property)
- Given , to find any pre-image such that .
- But remember: there are no known provably one-way functions.
- Second pre-image resistance (Weak collision resistance)
- Given , to find a 2nd-preimage where such that .
- Collision resistance (Strong collision resistance)
- Find any where such that .
- Need to guess inputs before finding a collision (birthday paradox).
- Examples:
- MD5: 128-bit hash
- SHA-1: 160-bit hash
- SHA-2 (SHA-256): 256/384/512-bit hash
- SHA-3
- Attack
- Dishonest signer
- Signs , later claims signed instead.
- Dishonest verifier
- Gets signature on , later claims signature on .
- Dishonest signer
5.2 Classification
- keyed
- Message authentication (MACs)
- Other applications
- Unkeyed
- Modification detection (MDCs)
- One-way hash function (OWHF)
- Preimage and 2nd-preimage resistance
- Collision resistant hash function (CRHF)
- 2nd-preimage and collision resistance
- because of birthday paradox ().
- Assumptions: operations are infeasible.
- One-way hash function (OWHF)
- Other applications
- Modification detection (MDCs)
5.3 How to build a hash function
- Modular arithmetic
- Block ciphers
- Dedicated design
5.4 General structure of iterated Hash Functions
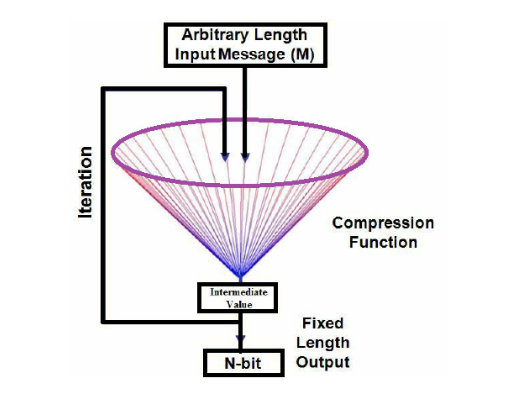
The Merkle–Damgård (MD) Construction of hash functions
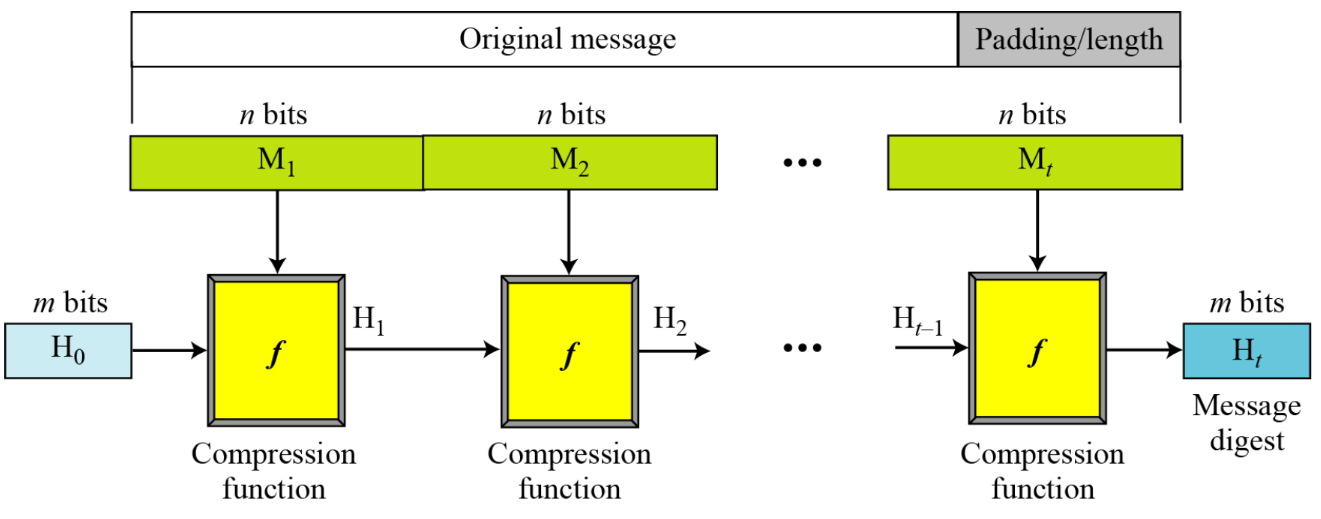
How
- Padding, because compressions functions cannot handle inputs of arbitrary size.
- Divide into equal parts.
Properties:
- If is collision resistant, so is .
5.5 Hash functions based on block ciphers
- Why
- Trust
- Reduce design, evaluation, and implementation effort
- Compact implementation
- Why not
- Slow
- weaknesses which are not relevant to encryption
- Block cipher could become weaken when used in .
5.6 Applications
- Data integrity
- Messages
- Files
- Confirmation of knowledge
- Passwords
- PRBGs: Cryptographically secure pseudo-random bit sequences generator
- Hash functions are designed to be “random functions” of the input.
- Examples:
/dev/random,/dev/urandom(Linux)- Acting as an entropy pool.
/dev/randomblocks when no bits available, but/dev/urandomkeeps going by SHA-1 (later by ChaCha20).
- Seed
- Avoid to use a simple value that an attacker could guess, e.g.:
- System time
- Process ID
- Avoid to use a simple value that an attacker could guess, e.g.:
5.7 Pre-computation attacks (Rainbow-table hash-chain attacks)
- How to
- Pre-compute all hash values under given inputs, and only store some fraction to save space (space-time tradeoff) to optimize future search.
- Variable-length messages do not generally have this problem, since input space is large
- Example: passwords have a fixed size, rainbow-table can be applied.
- Protect against pre-computation: salts
- Random value prepended to prior to calculating hash: .
- So an attacker would need to build a table for each possible salt value.
6. Message Authentication Code (MAC)
6.1 What it is
- Keyed hash functions are called MACs, which use both and a key as input.
- Why need it
- Encryption alone does not provide data integrity.
- Goal
- add authentication to the hash-value by using a secret (symmetric) key.
- Properties
- Should be difficult to create a valid MAC without knowledge of secret key
- Usage
- Message authentication: Alice sends
- Message authentication and confidentiality, where authentication is tied to:
- Plaintext:
- Ciphertext:
- Weakness: Does not provide non-repudiation
6.2 MDC vs MAC
- MDC should not be used for a MAC
- : length-textension attack
- is an interated MDC with compression function .
- is an attacker-controlled message.
- Attacker can computer to obtain without knowing .
- : collision
- Collision in the hash function will lead to a collision in the MAC.
6.3 Hash-based MAC
- is the key padded with zeros on left so it has length of 1 block for compression function.
- are distinct repeated byte strings of length
- any cryptographic hash function
- SHA-3 itself is immune to length extension attacks, so would be sufficient.
6.4 MAC from block ciphers: CBC MAC
- Problematic if
- Weak block cipher is used (e.g. DES)
- Message length is variable
6.5 Password-Based Key Derivation Function (PBKDF2)
- : hash or MAC function
- : Password
- : Salt value
- : Number of iterations
- : required key length
7. Public Key Cryptography and SSL
7.1 Overview
- Why
- In symmetric key systems, we have to share a secret key that nobody else knows.
- Split this key into two pieces, one is public, the other is private.
- How
- Uses number theoretic concepts: factoring, quadratic residue, RSA/DH problems
- It is asymmetric cryptography.
- Symmetric vs. public key Cryptography
- Keys in symmetric cryptosystem
- random bit strings
- no special mathematical properties
- generation is relatively easy
- Keys in asymmetric cryptosystem
- have speical mathematical properties
- generation is computationally expensive
- Key sizes are not comparable
- RSA-1024
- AES-128
- But still AES-128 is better
- Keys in symmetric cryptosystem
- Advantages
- Only private key must be secret
- Still, authenticity of public key must be guaranteed.
- The number of keys required is smaller than if symmetric keys used in large networks.
- Symmetric: Every pair of 2 people need a different key,
- Public key system: Every one has a key pair:
- Only private key must be secret
- Disadvantages
- Speed: Encryption is much slower than symmetric ciphers.
- Key sizes are typically much larger
- No public key cipher proven to be secure (although the same can be said for block ciphers)
7.2 Public Key Cryptography
- Uses two different keys: one publie , the other private
- Alice generate only known to her.
- Alice generate which she publishes, avaliable to both Bob and Oscar.
- Knowledge of does not reveal , or even given an advantage to Oscar trying to find .
- Alternatvie notation for Alice's keys: .
- Theory: trapdoor one-way function
- A function is a trapdoor one-way function if and only if is a one-way function.
- Given some extra information, it becomes feasible to compute .
- Public key cyrptography relies on trapdoor one-way function.
- Applications
- Encryption: let anayone send you a message that only you can read.
- Signature: let anyone verify that a message is from you.
7.3 Public Key Encryption
- Public-Private Key Pairs Properties
- Should be infeasible to find decryption key given encryption key and algorithm.
- Public key schemes utilise problems that are easy (P type) in one way but hard (NP type) in the other way, eg:
- Exponentiation vs. logs
- Multiplication vs. factoring
- How
- Alice wants to send a message to Bob. She knows his public key since it is public.
- Alice encrypts using producing .
- Bob decrypts using , a private key generated by Bob that corresponds to .
- Only can decrypt a message encrypted with .
- Notice this means that even Alice cannot decrypt .
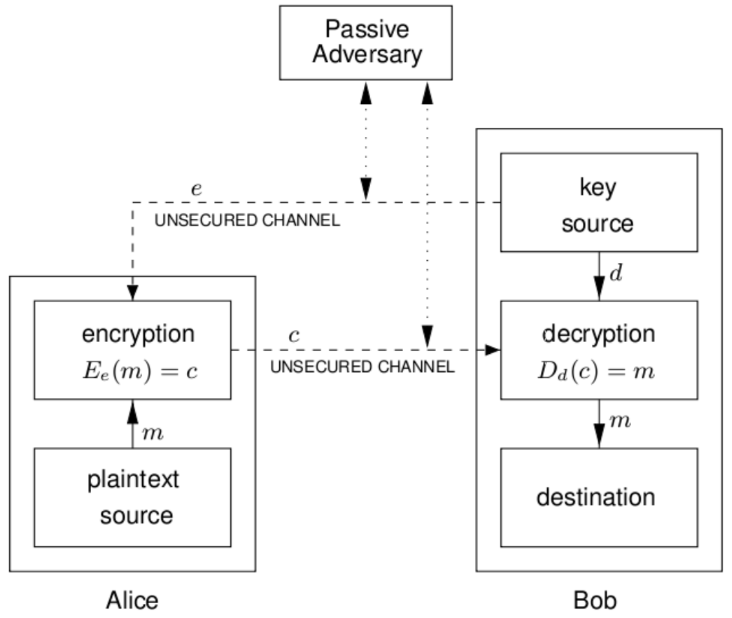
- Attack: Man-in-the-middle attack (MITM)
- Substitute different public keys between two users
- Adversary:
- All public key systems are vulnerable to MITM, must use authentic public keys.
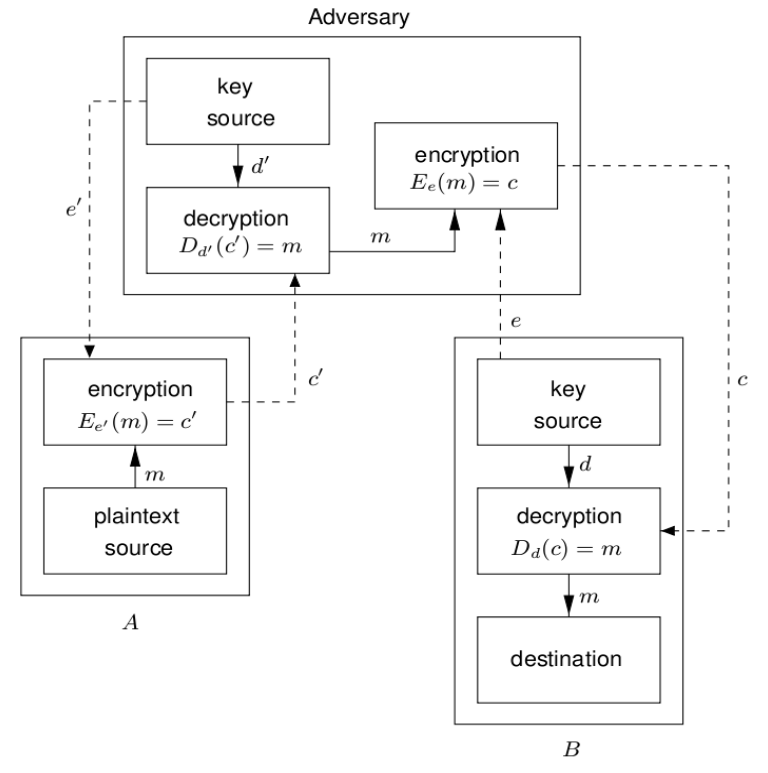
7.4 Public Key Signatures
- Signatures are for integrity and authentication of a message.
- Alice uses her private key to sign to produce .
- Bob uses Alice's public key to verify .
- Typical usage mode:
- Practically, the entire message is not encrypted with a public key, or signed with a private key
- Reason: Computational expense
- Encryption: encrypt a symmetric key using the public key, then the message encrypted with the symmetric key.
- Signature: sign instead of .
- Practically, the entire message is not encrypted with a public key, or signed with a private key
7.5 Diffie-Hellman Key Exchange (D-H Key Exchange)
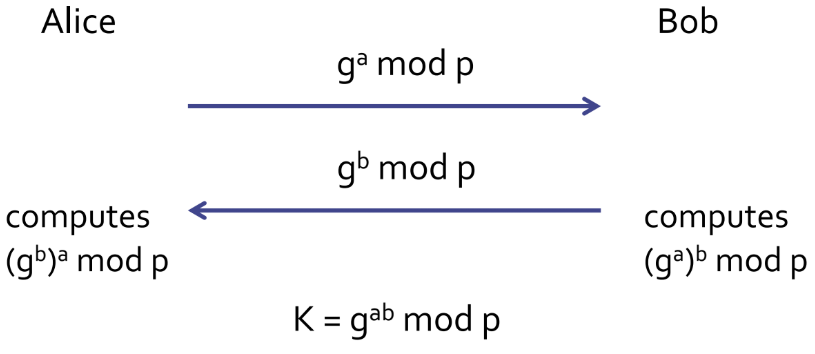
- Overview
- Enables two parties to jointly establish a shared secret key, no prior shared secret
- Based on exponentiation in a finite field (modulo a prime)
- Weakness: no authentication
- Security relies on the difficulty of computing discrete logarithms (similar to factoring)
- How it works
- , a large prime integer, public
- , a primitive root mod , public (also called a generator)
- Session key is then obtained by both parties calculating:
- are private to Alice and Bob respectively
- Alice can compute
- Bob can compute
- Attack
- The attacker needs either or to compute .
- Or Man in the Middle
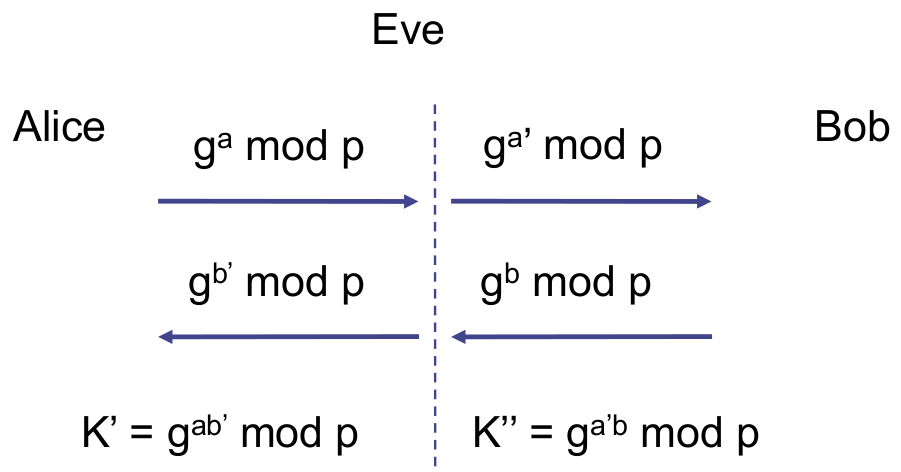
- D-H Man in the Middle
- Why it works? No authentication
- How it works?
- Alice sent , Eve sent , Bod received
- Bob sent , Eve sent , Alice received
- How it can be solved?
- Sign the and because the sign key is private.
- But have to share the key, leads to new problem
7.6 Password Authenticated Key Exchange
Definition
- Two parties share only a weak/low-entropy secret, e.g., a password
- Establish a secure channel between the users using only the shared secret and mutual authentication
- The channel must be protected by a high-entropy session key
- Offline guessing attacks on the weak secret must be infeasible
But how to derive a high-entropy secret from a low entropy one?
Example
- Password: 8 bits
- Generation: sha256(password) generates 256 bits to be used as a key
- But no need to guess
- Still only guess , then use sha256 to generate a key to test (need a testable sample)
Authenticated Diffie-Hellman (DH encrypted key exchange)
Shared passwod
Achieves:
- Mutual authentication
- Strong session key
- No offline attacks on PWD
- Key confirmation
7.7 RSA
- Theory
- Based on intractability of the integer factor factorization problem
- Key generation
- Generate 2 large and distinct primes and , each roughly the same size.
- What if one number is not large? (Then, would be too easy to find the other number)
- Compute and .
- is a relative prime to .
- e.g.:
- is a relative prime to .
- Select a random integer $e: 1< e < \Phi(n) $
- gcd
- can be small for encryption efficiency.
- Use extended Euclidean algorithm (HAC) to computer the unique integer , such that .
- Keys
- Public key is .
- Private key is .
- Generate 2 large and distinct primes and , each roughly the same size.
7.8 RSA Encryption
- How it works
- Bob encryption
- Get Alice's authentic public key
- Take the message and represent it as an integer in the interval .
- If cannot be represented in , separate into blocks.
- Computer .
- Send to Alice.
- Alice decryption
- Compute .
- Bob encryption
- Why it works
- Since , there exists an integer such that
- Euler's theorem: where
7.9 Digital Signature
- Scheme:
- a secret signing key and a public verfication key
- Service provided:
- Authentication
- Data integrity
- Non-Repudiation (MAC does not provide this)
- , ?
- , because the private key is from the signer
- Problem
- How do we obtain someone's public key over a network, in a way that we can trust it belongs to the claimed entity?
- Certificates
- Relies on a set of trusted third-party certificate authorities to establish the authenticity of certificates.
- Source is normally a trusted third party (also called: certificate authority (CA)).
- Root certificates are self-signed.
- Categories
- With appendix: the signature of the message is usually appended to the unmodified message . So or is sent.
- With message recovery: all or some of the message is embedded in the signature. When all of the message is embedded, the verification procedure requires only as input, and recovers as a by-product (that's known as total message recovery). Only the signature is sent; it embeds the message.
7.10 RSA Signature
- Overview
- : a redundancy function, maps message to RSA inputs.
- No confidentiality: anyone with Alice's public key can recover the message .
- Authentication and integrity guarantees: only the holder of Alice's private key can create a valid mesage that has a signature verifiable with her public key.
- How it works
- Alice wants to sign a message :
- Computes .
- Computes .
- Alice's signature for is .
- Bob wants to verifty:
- Obtains Alice's public key .
- Computes .
- Verifies that is in the redundancy space.
- Recovers .
- Alice wants to sign a message :
- RSA signature with Appendix
- Alice calculates .
- Alice signs .
- Alice transmits .
- Bob can verify message by calculating and comparing to the verified signautre.
- PGP (Pretty Good Privacy) uses it to create signautre on email.
7.11 SSL
- Properties
- What it has
- Confidentiality
- Message authenticity
- Authentication
- Server authentication
- Client authentication
- What it hasn't
- Non-repudiation
- Availability
- What it has
- Architecutre
- between Application layer (HTTP/LDAP/POP3) and Transport layer (TCP)
8. Usability and human factors in security
8.1 Pretty Good Privacy (PGP)
Steps:
- Install PGP/GPG/OpenPGP
- Generate/import key pairs
- Protect your private keys
- Integrate/enable in your mail client
- Publish your public key
- Collect public keys of your contacts
Encryptoin/Decryption
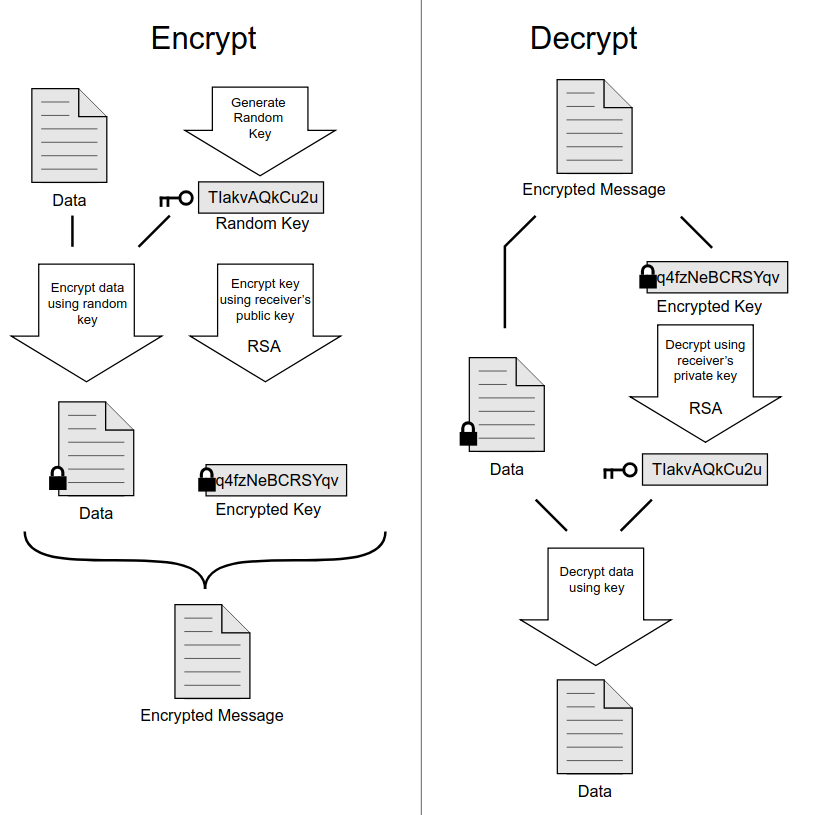
Why Johnny Can’t Encrypt: A Usability Evaluation of PGP 5.0
- Hypothesis: effective security requires a different usability standard, and that it will not be achieved through the user interface design techniques
- Conclusions:
- “making security usable will require the development of domain-specific user interface design principles and techniques”
- “user interface design for effective security remains an open problem”
- Usability for security: Security software is usable if the people who are excepted to use it:
- are reliably made aware of the security tasks they need to perform;
- are able to figure out how to successfully perform those tasks;
- don't make dangerous errors; and
- are sufficiently comfortable with the interface to continue using it.
- Problematic properties of security
- The unmotivated user property
- Secondary goal (security is not important)
- Optimistic view (security is working; nothing to hide)
- Get help from psychology studies (user capabilities: users cannot remeber long password or users do not know a strong password; how to motivate people)
- The abstraction property
- Policies are abstract
- Policies vs. implementation
- The lack of feedback property
- How to design effective warning dialogs
- How to communicate system state
- Too much feedback can also be bad
- The barn door property
- Once a secret has been left accidentally, even for a short time, it's useless now.
- The weakest link property
- A single user error is enough to defeat a system
- Users must follow all security guidelines
- The unmotivated user property
- Expected usability standard for PGP
- understand encrypt/decrypt
- understand authentication
- understand generate key pair
- understand publish their public key
- understand acquire public keys
- manage to avoid dangerous errors
- be able to succeed at all of the above within a few hours of reasonably motivated effort.
- PGP's usability evaluation methods
- Cognitive walkthrough
- Simulated use by a domain expert
- Step throug the use of the software
- Learnability evaluation
- Cognitive walkthrough: Findings
- Irreversible actions
- Accidentally deleting the private key
- Accidentally publicizing a key
- Accidentally revoking a key
- Forgetting the pass phrase (public keys collected from others)
- Failing to back up the key rings
- Sending a message to wrong recipients
- Sending a confidential message as plaintext
- Failing in signature verfication
- Failong in revocation check
- Trusting the wrong keys
- Consistency of terminologies
- Encoding vs. encrypting
- "Too much information"
- Define what is important and what is not
- Basic, intermediate, and advanced levels in UI
- Irreversible actions
- User study
- Test with real users
- User study results
- Dangerous errors
- 3/12 sent confidential message in plaintext
- 2 realized the mistake; one did not
- 1 forgot the passphrase
- Figuring out how to encrypt with any key
- 1/12 failed to encrypt at all
- 2 took close to half an hour
- Figuring out the correct key to encrypt with
- 7/11 used their own keys
- 1 generated key pairs for others
- Decrypting an email message
- 2/5 succeeded
- Deciding whether to trust keys from the key server
- 3/8 members expressed concern
- Dangerous errors
- Cognitive walkthrough
8.2 Human as an attack vector
- Why
- Real attacks exploit psychology and technology
- Phishing, vishing
- Targeted vs. generic
- Easy to launch online "imitation" attacks
- Deception history
- Attacker's goals
- Information extraction
- malware infection
- APT (Advanced persistent threat)
- Long-term attack vector
- Stealth
- monetary gains
8.3 Phishing
- Why
- Natural trust: attacks via "trusted" contacts
- Target the vulnerables: elderly, young-adults, low-income
- Fit with natural work-flow
- How to detect phishing emails when banks also send similar emalis
- Greed
- Social validation
- Phishing user study
- Good phishing websites fooled 90% of participants.
- Existing anti-phishing browsing cues are ineffective.
- On average, the participant group made mistakes on the test set 40$ of the time.
- Popup warnings about fraudulent certificates were ineffective.
- Neither education, age, sex, previous experience, nor hours of computer use showed a statistically significant correlation with vulnerability to phishing.
- Analysis of past attacks
- Victims' lack of knowledge
- Visual deception
- Bounded attention
- Too many indicators for different types of security issues
8.4 The RSA SecureId Hack (Hardware authentication token)
- What it is
- Hardware authentication token
- Dynamic code
- Use of RSA SecurID
- Second factor
- Side notes: three factors of authentication
- Something you know, have, are
- Issue
- Auth servers must be in sync and hall all seeds
- Biometrics authentication
- Once compormised, it cannot be replaced.
8.5 Deception
- What it is
- Planned actions to mislead attackers and
- To cause them to:
- Confuse
- Take/avoid specific actions
- Must be mixed with some “truth”
- Attackers must be given “hope”
- Advantages
- False info can reduce value of leaked databases
- Learning the attacker’s moves
- Slow down the attacker
9. Botnets and DDoS
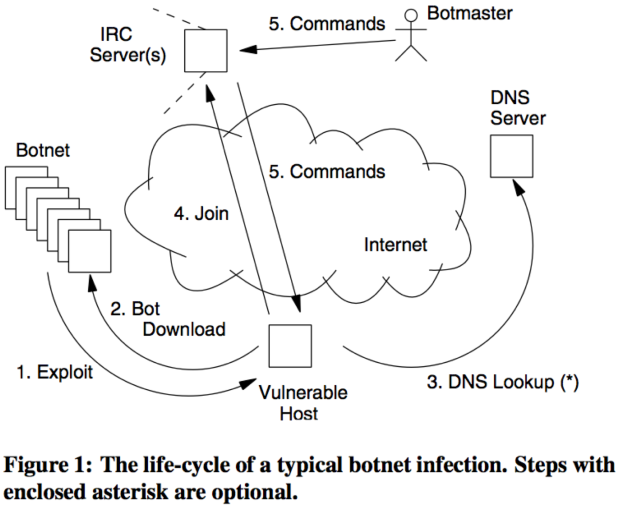
9.1 Botnets
What it is
- Bot v.s. malware
- Bot is controlled by someone remotely
- malware not
- Botnets: networks of infected end-hosts, called bots, that are under the control of a human operator commonly known as a botmaster.
- Bot software: advanced malware that makes the funcationality of a compromised host available to the botmaste.
- Bot v.s. malware
Features
- propagate like worms
- hide from detection like many viruses
- attack like many stand-alone tools
- have an integrated command and control system
How to infect
- "curious George" attacks
- Backdoors from a previous infection
- Trojaned applications
- OS/browser/application vulnerabilities
- Open file shares
- P2P networks
How to control:
Centralized
* Better control* Efficient attacks* Single-point vulnerability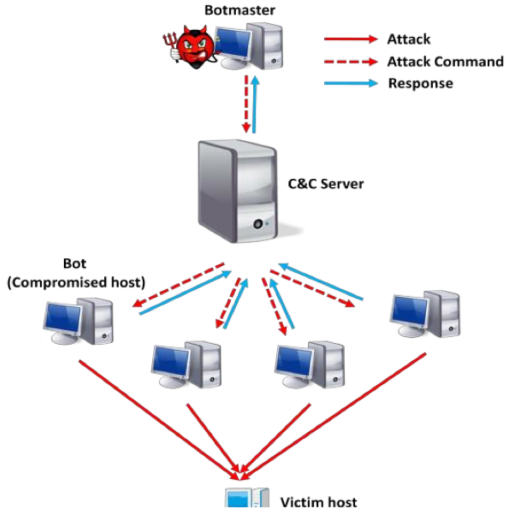
P2P
* robust againt disruption* Inefficient* unreliable from attackers' viewpoint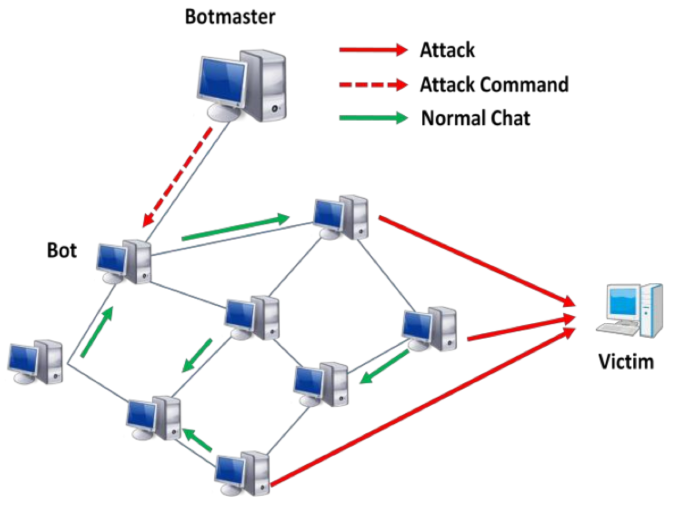
Hybrid: mixture of centralized and P2P
How to protect masterbot: Dynamic domain names
- A single domain is problematic
- Multiple domains do not help
- Names can be learned in advanced and blocked
- Bots can be reverse-engineered to extract domains
- Domain Generation Algorithms (DGA)
- Generate domain names depending on one or more external information sources serving predictable seed values that can be accessed by bots and botmasters.
- Seed values: timestamp, Twitter trends
Detection
- Passive techniques
- Active techniques
- Sinkholing: Redirecting or dropping traffic destined to a C&C server, malware distribution server or attack server.
- Reverse engineering of bots
9.2 DDos attacks
- DDos can:
- Degrades a resource used by a victim (legitimate user) or
- Denies use of a resource by a victim
- Clog/crash a resource
- Target resources:
- network bandwidth,
- CPU,
- database/disk bandwidth
9.3 DDos Attack methods
SYN floods
- When TCP establishs a connection, it would handshake first:
- TCP three-way handshake: SYN, SYN-ACK, ACK
- Half-open connections: SYN, SYN-ACK
- Weak point
- Each SYN packet (new connection) mandates the server to allocate resources
- Attack
- Attack on the memory
- Fake/genuine IP addresses can be used to sent tons of SYN packets
- When TCP establishs a connection, it would handshake first:
Application-based attacks
- HTTP flood
- Generally launched from a botnet (need genuine IP, because have to establish the connection first)
- Attack
- Attack on the bandwidth and CPU
- Large files requests
- Search service of a site
- Complex queries
- HTTP flood
DNS amplification attack
How it works
Compromise an authoritative DNS server and publish a large TXT record
TXT record: a type of resource record in the Domain Name System (DNS) used to provide the ability to associate arbitrary text with a host or other name, such as human readable information about a server, network, data center, or other accounting information.
example.com IN TXT "This domain name is reserved for use in documentation"
The attacker uses botnet to send UDP packets with spoofed IP addresses to a DNS recursor. The spoofed address on the packets points to the real IP address of the victim.
Each one of the UDP packets makes a request to a DNS resolver, often passing an argument such as “ANY” in order to receive the largest response possible.
After receiving the requests, the DNS resolver, which is trying to be helpful by responding, sends a large response to the spoofed IP address.
The IP address of the target receives the response and the surrounding network infrastructure becomes overwhelmed with the deluge of traffic, resulting in a denial-of-service.
Difficult to prevent
- Millions of open recursive DNS servers
- High capacity servers ("fat" bandwidth)
- DNS servers are not directly affected – no incentive to adopt known "good practices"
- may not need to compromise an authoritative DNS server
9.4 Mirai attack
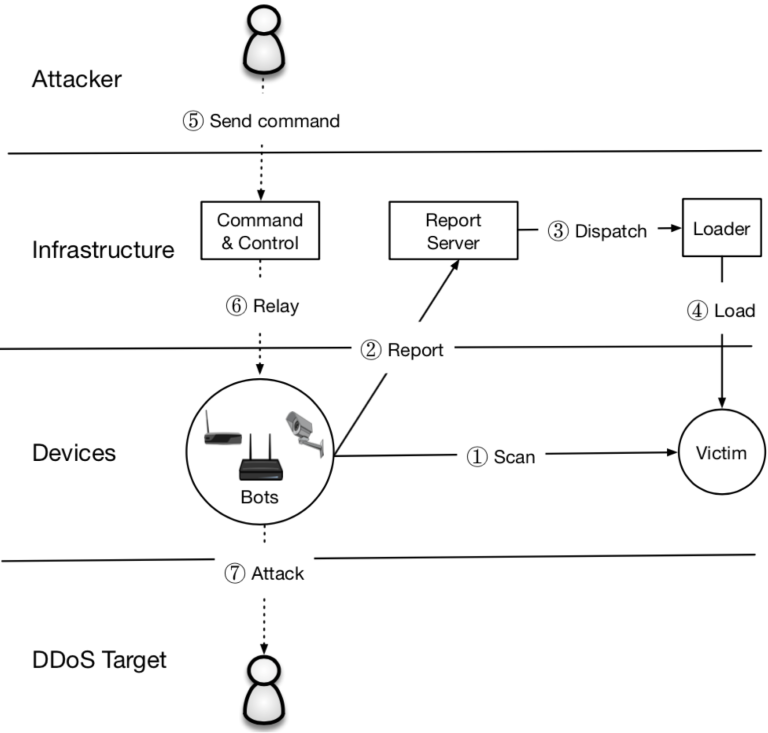
- Scan: sent TCP CYN probes to pseudorandom IPv4 addresses, excluding blacklist.
- Why scan? and scan efficient?
- Stateless: no memeory allocation. But if recevied any response from any device, that device is a potential victim.
- Why scan? and scan efficient?
- If a potential victim is found, starts a brute-force login phase.
- Use preconfigured dictionary, because resource is constrained.
- Send the victim's IP and associated credentials to Report Server.
- Report Server dispatches the command to Loader.
- Loader will try to login the victim devicem then try to find out what kind of this device is.
- Loader will send corresponding binary to the victim, and the victime would join the botnet.
- Finally, the attacker would use the botnet to launch other attacks.
13. Domain Fronting
What
- Circumvents Internet censorship by obfuscating the domain of a HTTPS connection
- Allows a user to connect to a blocked service (via DNS, IP or deep packet inspection)
- uses different domain names at different layers of communication
- In an HTTPS request, the destination domain name appears in
- the DNS query,
- the TLS Server Name Indication (SNI) extension,
- and the HTTP Host header
- For
- regular connections, the same domain name is used.
- domain-fonted connections, HTTP Host has the true destination domain.
Techniques
- With a front domain name:
- Domainless fronting
14. Write Protection Against Privileged Data Tampering
14.1 Legacy solutions
- detection via anti-malware
- key recovery via reverse engineering
- backup
14.2 Academic proposals
- monitoring file I/O activities
- recording encryption keys
- shadowing file writes
14.3 FlashGuard
- relies on intrinsic properties of SSD writes
- cannot deal with data destruction malware
14.4 Data loss prevention
- Trusted environments
- TEE-Disk: Self-encrypting devices
- Fine-granined access control
- programmable control (lock-unlock)
- TEE-Host: Intel TXT or AMD SVM
- Dynamic root of trust, measured, isolated
- Sealed secret (platform state binding)
- Device I/O access
- TEE-Disk: Self-encrypting devices
- Design
- Stand-alone: occasional interruptions due to TXT exclusiveness
- Network-based: any user device, no interruptions
- Space cleanup
- Automatic stale version deletion
- Mini file browser: manual file deletion (within the trusted updater)
- Challenges
- Safely use I/O devices from the user OS
- Programming the SED OPAL interface
- DMA access in TEE
- Porting Flicker to Windows 10 64-bit
- Security
- Outside the trusted environment, can malware update files on the protected partition?
- Inside the trusted environment, can malware trick the updater to write arbitrary content?
- Attacks to consider
- Forged UI
- Termination
- Flaws in TEE implementations
- Persistent attacker (delayed attacks after deletion)
Tutorial 9 - RSA/AES encryption with OpenSSL
Public key crypto
Release your public key
Usage:
- Encryption
- Anyone encrypts using your public key
- Nobody can decrpty but you with your private key
- Signature
- You sign some data with your private key
- Anyone can verify your signature with your public key
RSA encryption/decryption with OpenSSL
Generate key
Steps
- Extract the public key
- (Optional) look at Alice's public key
- Pass the public key to Bob
- Bob encrypt the message with Alice's public key
- Bob pass the encrypted message to Alice
- Alice decrypt the message with her private key
Problem
- Computation expensive
- Plaintext's size should be smaller than the modulus (2048)
Solution
- Hybrid encryption: Asymmetric and symmetric encryption
- RSA encrypt a symmetric key to encrypt secret
AES encryption/decryption with OpenSSL
Steps
- Bob generates a random AES key and IV:
32bits (key size for AES-256)16bits (block size for AES-256)
- Bob encrypts the message with his own AES key and IV
- Bob encrypts the AES key and IV with Alice's public key
- Bob send
aes.key.enc, aes.iv.enc, secret.txt.encto Alice - Alice decrypts the AES key and IV
- Alice decrypts the encrypted message
Alternative Steps
- Use PBKDF2 to simplify key and IV generation
- Bob eenerate a password randomly
- Bob encrypts using a file as password
- Bob encrypts the password file with Alice's public key
- Bob send
pass.key.enc, secret.txt.encto Alice - Alice decrypts the password file
- Alice decrypts the secret using the password file